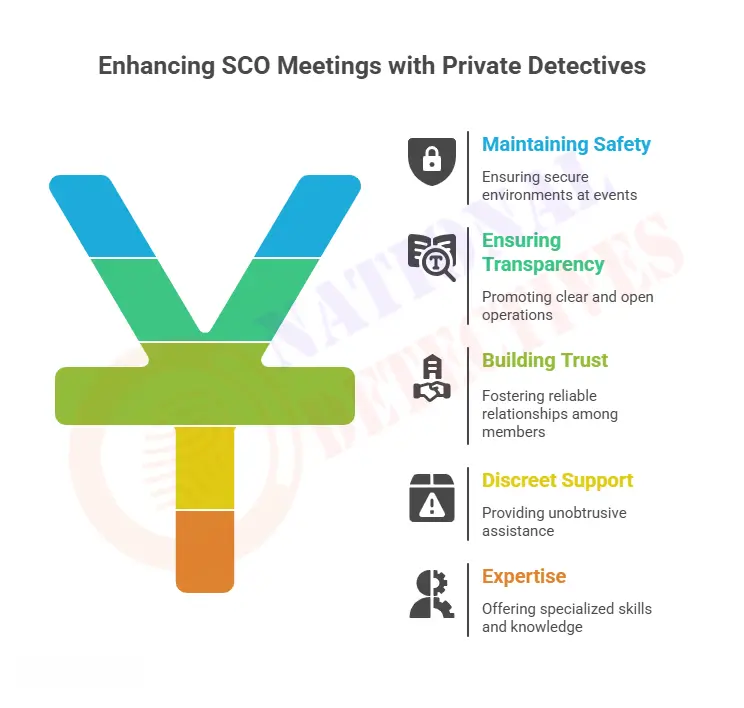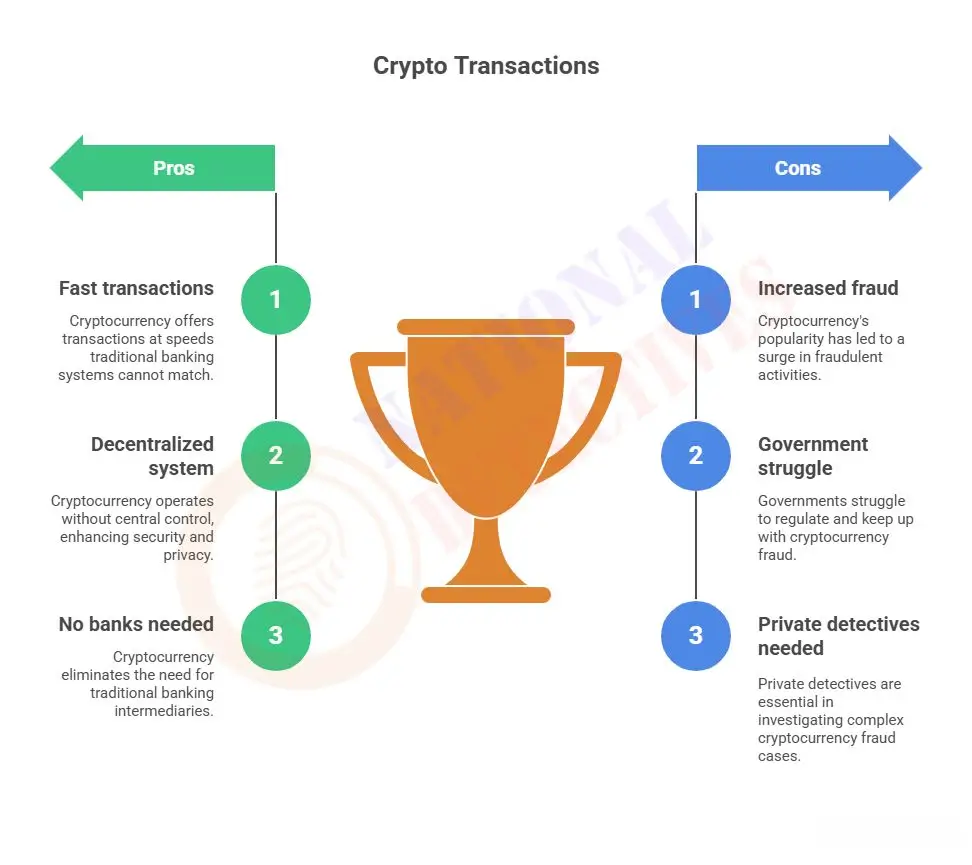
Information is power, and much of that data can be freely found online by anyone with knowledge about where and how to look. Open Source Intelligence (OSINT), an increasingly useful technique used by private detectives, law enforcement personnel, corporate investigators, journalists and even governments is an indispensable source of intelligence gathering and analysis.
OSINT involves gathering, analyzing, and using publicly accessible sources as sources for investigations. While OSINT doesn't involve hacking or illegal access, it often uncovers patterns, connections and truths missed by traditional surveillance.
What Is Open Source Intelligence (OSINT)?
OSINT stands for Open Source Intelligence and refers to data sourced from legally accessible public resources that is legally accessible for everyone - this may include things such as websites and public databases that legally make their data publicly accessible such as Wikipedia and online polling websites such as Survey Monkey. This could include anything from gathering intelligence on political campaigns from these sources through geofencing techniques through to gathering intelligence information sourced directly from official government records that legally available public sources may contain such sources:
-
Social Media Platforms (Facebook, LinkedIn, Instagram and X/Twitter, among other social networking services).
-
Public Databases and Government Portals. News Articles and Archives
-
Forums Blogs Dark Web Indexes WHOIS and Domain Records. Satellite Imaging Geo Tagging Content in YouTube Tik Tok etc
OSINT seeks to develop comprehensive intelligence profiles without breaking any laws or needing a warrant for actionable intelligence gathering.
Why OSINT Matters in Investigations
OSINT provides invaluable solutions when investigating Corporate Investigation fraud, financial crime or threats to national security.
-
Speed and Cost-Efficiency: When compared with traditional surveillance techniques, OSINT offers faster, cheaper, and often more informative monitoring solutions.
-
Anonymity: Investigators can collect large volumes of information without raising suspicion by gathering it anonymously without physically being present or raising any red flags.
-
Verification and Lead Generation. OSINT can facilitate cross-verification of identities, claims, timelines and timelines against digital footprints. Lead Generation. OSINT assists investigators by leading them toward deeper targets such as finding alternate accounts or physical addresses to pursue.
Common OSINT Techniques
1. Social Media Profiling
-
Tracking real-time activity such as check-ins and hashtag usage.
-
Discovering alternate or fake profiles.
-
Extracting deleted or archived posts via tools such as the Wayback Machine
2. User and Email Tracking Information
-
Searching username reuse across platforms to link multiple accounts together.
-
Tracking email leaks or associated data through breach databases like HaveIBeenPwned (HAVPWNED).
3. Understanding Phone Number Intelligence
-
Reverse phone lookups to identify SIM ownership or messaging patterns; using WhatsApp, Truecaller or Telegram group links as entryways into communication hubs;
4. Geo-Location and Mapping
-
Extracting locations from image metadata (EXIF).
-
Utilising satellite images or open platforms such as Google Earth for surveying.
-
Triangulating movement patterns using check-ins or geotags.
5. Domain and Website Analysis
-
Tracking domain ownership through WHOIS.
-
Discovering hidden connections among websites using IP sharing and digital fingerprinting technologies.
6. Deep and Dark Web Scanning
-
Investigating leaked documents, forums or black-market dealings.
-
Monitoring illicit chatter using Tor-based search tools.
Tools of the Trade
There are various OSINT tools which have become ubiquitous over time, but here are a few that standout:
-
Malthusian and Shodan can both provide link analysis and relationship mapping features, while SpiderFoot automates OSINT data collection processes while Recon-ng provides an open-source reconnaissance framework
-
IntelX and Google Dorks: Tools designed to quickly search leaked databases and darknet content.
-
Google Dorks: Special search queries designed to unearth hidden information on websites
Case Studies for Private Detectives
-
Marriage and Background Checks
-
Verifying employment claims, checking relationships for hidden children or former partners, and monitoring online behavior through social media footprints is crucial for maintaining employment claims, verifying hidden relationships and tracking online behavior through digital footprints Pre Matrimonial Investigation.
-
Corporate Due Diligence
-
Validate company operations, identify shell corporations, evaluate litigation histories or detect relationships among rival businesses.
-
Legal Support
-
Whilst finding assets or uncovering conflicts of interests may require professional services for civil or criminal cases. Arranging Legal Documents for Trial
-
Threat and Risk Intelligence
-
Unveil online threats, monitor stalking behavior and activist discourse or prevent corporate espionage by employing our technology tools and solutions.
-
Locating Missing Individuals
-
Analysing digital trails, mapping online interactions or pinpointing recently visited locations are effective strategies for tracking people down.
Legal and Ethical Boundaries
Investigators utilizing OSINT from public sources must remain within ethical and legal constraints when gathering this intelligence. Key points:
-
Consent isn't always required when sharing publicly shared data; however, any breach into private domains (e.g. hacking or impersonation) requires explicit approval by those affected;
-
Jurisdictional differences in data laws such as GDPR or India's DPDP Act could impact what data may or may not be permissible in each instance.
-
Accuracy cannot be assured-investigators must verify findings from multiple angles for maximum reliability.
OSINT Has Its Limitations
-
Disinformation and noise: Public spaces are filled with false or misleading content that quickly circulates around them, along with time-sensitive data which can quickly disappear or change; whilst an overwhelming volume of data could overwhelm novice investigators.
-
False Positives: Misidentification may happen with names, emails or photos being mixed up as false positives.
Best Practices
-
Always document and date-stamp any findings.
-
Use multi-tool triangulation--don't depend solely on one source for evidence.
-
Respect privacy and ethical boundaries--no coercion, impersonation or unauthorised access!
-
To preserve legal use, evidence should be stored in formats which cannot be altered without being undone by anyone.
Conclusions OSINT Is The Key To Modern Detection
OSINT (Open Source Intelligence Network Tactics) has become an indispensable skill for private detectives. From verifying voter lists to uncovering corporate fraud or tracking cyber threats, this non-invasive and powerful technique gives Private investigators in Delhi a distinct edge against investigation.
Mastery of OSINT requires more than just tools; it involves analytical thinking, curiosity and the ability to connect dots others miss. Detectives who wish to remain competitive must invest heavily in developing robust OSINT capabilities as part of their ongoing strategies.